Minimal Lighthouse definition
An example Lighthouse definition with a minimal set of managed service roles that are also valid for ACR recognition via PAL.
Recap
- Include a PEC eligible role (such as Support Request Contributor) in your authorizations
- Include the assignment delete role
- Use security groups and service principals in the authorizations
- Avoid specifying individual users as this leads to unneccessary definition updates
- PAL link the individual users and service principals
You will then receive the ACR recognition for the positive impact of the service in those customer subscriptions.
⚠️ When onboarding new users, simply add them to the security group and create the PAL link. There is no need to update the Azure Lighthouse definition if you are using security groups.
Lab flow
The example minimal definition in the lab has three roles in the permanent authorisations:
In this lab:
- Azure Lighthouse definition
- review the example minimal definition
- customise your own service definition template
- As the customer
- create the managed service offer from the template
- delegate a subscription
- As the managed service provider
- see the multi-tenanted experience
- check that PAL is linked
Azure Lighthouse definition
In this section
- review the example minimal definition
- customise your own definition
Example template
The minimal definition below can be found in my lighthouse repo.
{
"$schema": "https://schema.management.azure.com/schemas/2018-05-01/subscriptionDeploymentTemplate.json#",
"contentVersion": "1.0.0.0",
"variables": {
"ManagedServicesRegistrationAssignmentDeleteRole": "91c1777a-f3dc-4fae-b103-61d183457e46",
"Reader": "acdd72a7-3385-48ef-bd42-f606fba81ae7",
"SupportRequestContributor": "cfd33db0-3dd1-45e3-aa9d-cdbdf3b6f24e"
},
"resources": [
{
"type": "Microsoft.ManagedServices/registrationDefinitions",
"apiVersion": "2019-06-01",
"name": "[guid('Azure Citadel - Basic Support Service')]",
"properties": {
"registrationDefinitionName": "Basic Support Service",
"description": "Azure support services for call logging and call management (L0/L1).",
"managedByTenantId": "3c584bbd-915f-4c70-9f2e-7217983f22f6",
"authorizations": [
{
"principalIdDisplayName": "Managed Service Management",
"principalId": "9d2b2ec1-a465-431f-91d3-546f97b8fb26",
"roleDefinitionId": "[variables('ManagedServicesRegistrationAssignmentDeleteRole')]"
},
{
"principalIdDisplayName": "Managed Service Consultants",
"principalId": "30f86a83-b2a9-477a-90d6-23e51042839a",
"roleDefinitionId": "[variables('Reader')]"
},
{
"principalIdDisplayName": "Managed Service Consultants",
"principalId": "30f86a83-b2a9-477a-90d6-23e51042839a",
"roleDefinitionId": "[variables('SupportRequestContributor')]"
}
]
}
}
]
}
Main properties
Here are the main top level properties for the Microsoft.ManagedServices/registrationDefinitions resource:
"resources": [
{
"type": "Microsoft.ManagedServices/registrationDefinitions",
"apiVersion": "2019-06-01",
"name": "[guid('Azure Citadel - Basic Support Service')]",
"properties": {
"registrationDefinitionName": "Basic Support Service",
"description": "Azure support services for call logging and call management (L0/L1).",
"managedByTenantId": "3c584bbd-915f-4c70-9f2e-7217983f22f6"
}
}
]
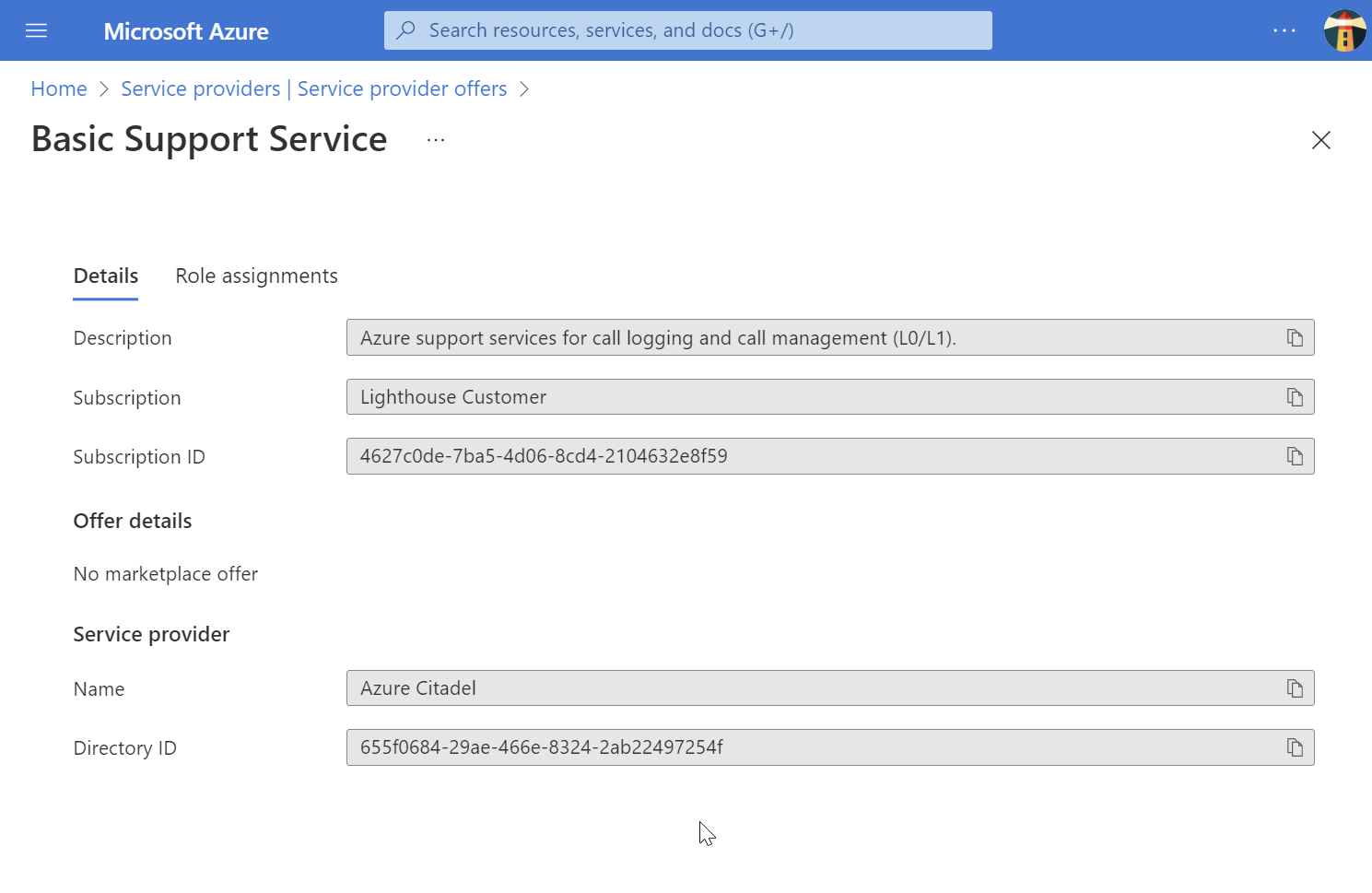
The registrationDefinitionName and description are cosmetic. The delegated resources will be projected to this the service provider’s managedByTenantId.
Note that the actual resource name is a GUID. Here we generate a predictable GUID using a function that takes a seed string.
This is how the Details tab will look in the portal.
Authorizations array
The template has the following authorizations array. The principalId is the objectId for the user, service principal or security group. The principalDisplayName is cosmetic.
"authorizations": [
{
"principalIdDisplayName": "Managed Service Management",
"principalId": "9d2b2ec1-a465-431f-91d3-546f97b8fb26",
"roleDefinitionId": "[variables('ManagedServicesRegistrationAssignmentDeleteRole')]"
},
{
"principalIdDisplayName": "Managed Service Consultants",
"principalId": "30f86a83-b2a9-477a-90d6-23e51042839a",
"roleDefinitionId": "[variables('Reader')]"
},
{
"principalIdDisplayName": "Managed Service Consultants",
"principalId": "30f86a83-b2a9-477a-90d6-23e51042839a",
"roleDefinitionId": "[variables('SupportRequestContributor')]"
}
]
The roleDefinitionId is the GUID for the Azure RBAC built-in roles. The template uses variables for readability.
"variables": {
"ManagedServicesRegistrationAssignmentDeleteRole": "91c1777a-f3dc-4fae-b103-61d183457e46",
"Reader": "acdd72a7-3385-48ef-bd42-f606fba81ae7",
"SupportRequestContributor": "cfd33db0-3dd1-45e3-aa9d-cdbdf3b6f24e"
}
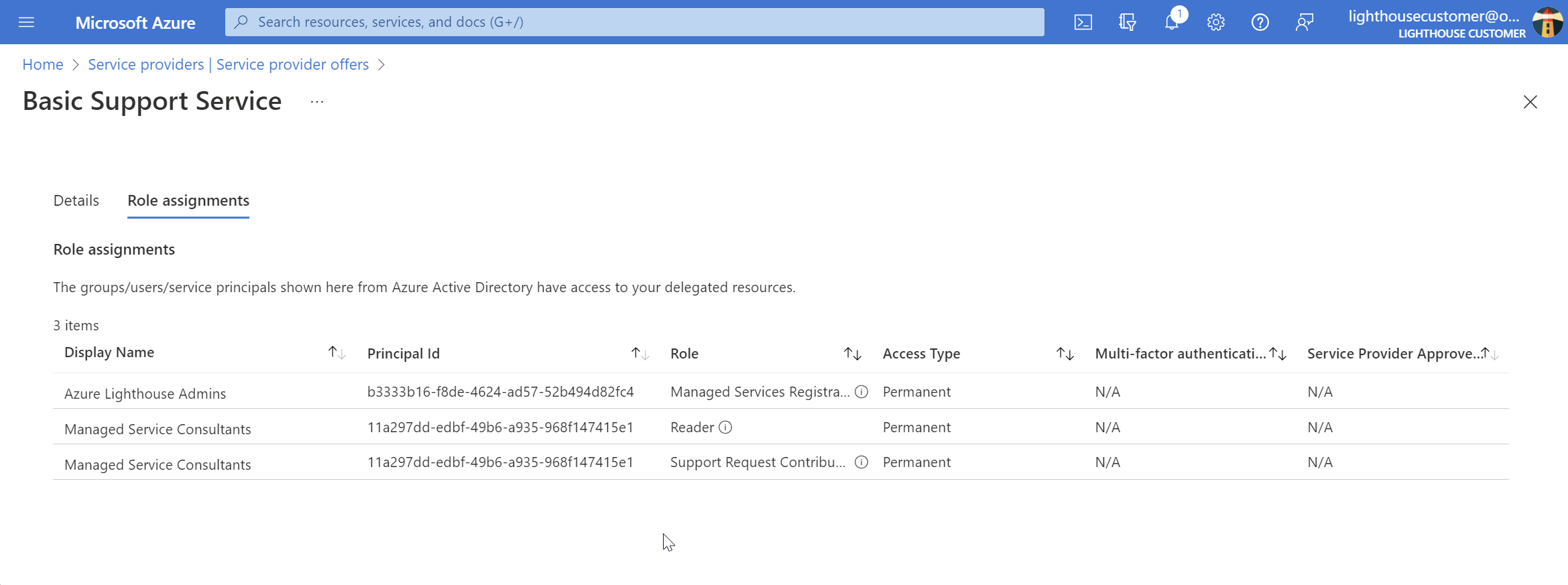
The Support Request Contributor role has an action, Microsoft.Support/*, which makes the role eligible for partner earned credit (PEC). All PEC eligible roles include write and/or delete actions. Read actions are insufficient for PEC eligibility.
Another important role in the authorizations array is the Managed Services Registration Assignment Delete Role. This allows the managed services provider to delete assignments assigned to their tenant. Without that role you would be forced to ask the customer to delete the assignment.
Note that there are limitations in the role support for Azure Lighthouse. You can only use in-built roles. You cannot use roles with dataActions. Owner cannot be used, and User Access Administrator is limited to assigning a defined set of roles to managed identities.
This is how the Role Assignments tab would look in the portal:
Customise your definition
⚠️ Please do not run the example template without customising it first! Use the example template as your starting point.
-
Save it locally and edit in your favourite editor.
We recommend Visual Studio Code with the Azure Resource Manager (ARM) Tools extension.
-
Update the
managedByTenantIdto match your tenantId -
Update the cosmetic descriptions
-
Create your own AAD security groups for
- Managed Service Managers
- Managed Service Consultants
You are not limited to these groups or descriptions. They are just used as an example.
-
Update the descriptions and objectIds in your template to match
-
Save your changes to a new filename e.g. myServiceOffer.json
Customer
⚠️ It is recommended to have your own test customer subscription (in its own tenant) for Azure Lighthouse testing and demos.
In this section, as the customer, I:
- create the managed service offer from the template
- delegate a subscription
Create a definition
- Click on Service provider offers in Azure Lighthouse’s service providers area
- Click on Add offer and Add via template
- Drag and drop the template, or browse to the file
- Deploy to create the definition
- View the offer in the Service provider offers list
- View the details
- View the role assignments
Create an assignment
- Click on either Delegations in the blade, or on the
+next to an offer - Select your subscriptions or resource groups
- Check the disclaimer box
- Delegate
Alternatives
I personally recommend the manual portal creation to partners who are onboarding new customers as it is quick and is a good way to demystify the process for customers. It is also reassuring to see the inbuilt roles and to know that
There are other ways to onboard customers via templates. You may also publish Managed Service offers to the Azure Marketplace.
The definition creation steps can be performed on behalf of the customer by partners in CSP subscriptions through their Admin Of Behalf Of (AOBO) permissions. CSP partners with AOBO can also parameterise a Microsoft.ManagedServices/registrationAssignments resource to automate the delegation.
Managed services provider
In this section:
- see the multi-tenanted experience
- check that IDs are PAL linked
Multi-tenancy
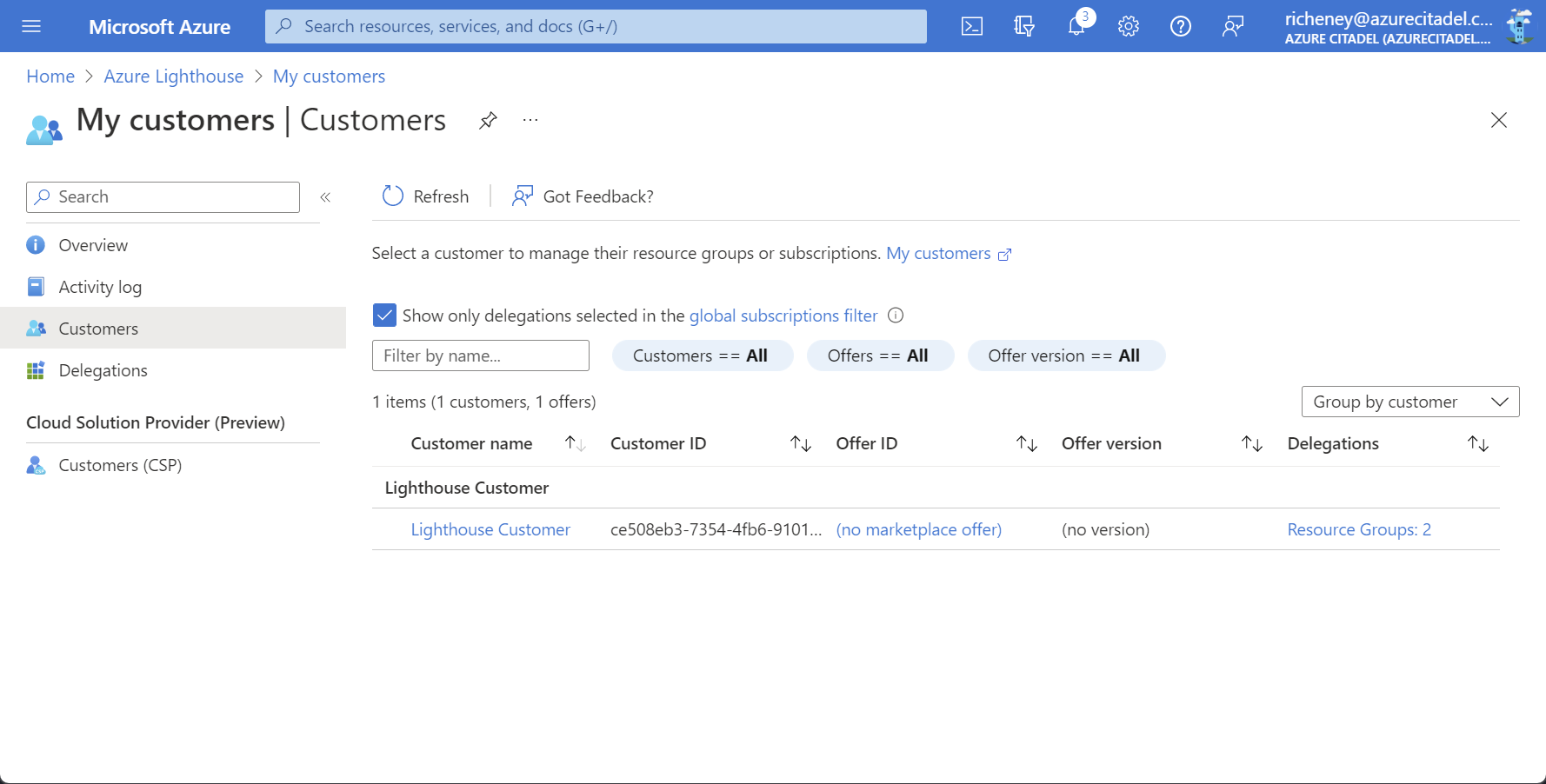
Wait for delegation to complete. Propogation can take a few minutes and you may need to log out and back in again.
-
Open the portal
-
View My Customers (Azure Lighthouse > Manage your customers)
-
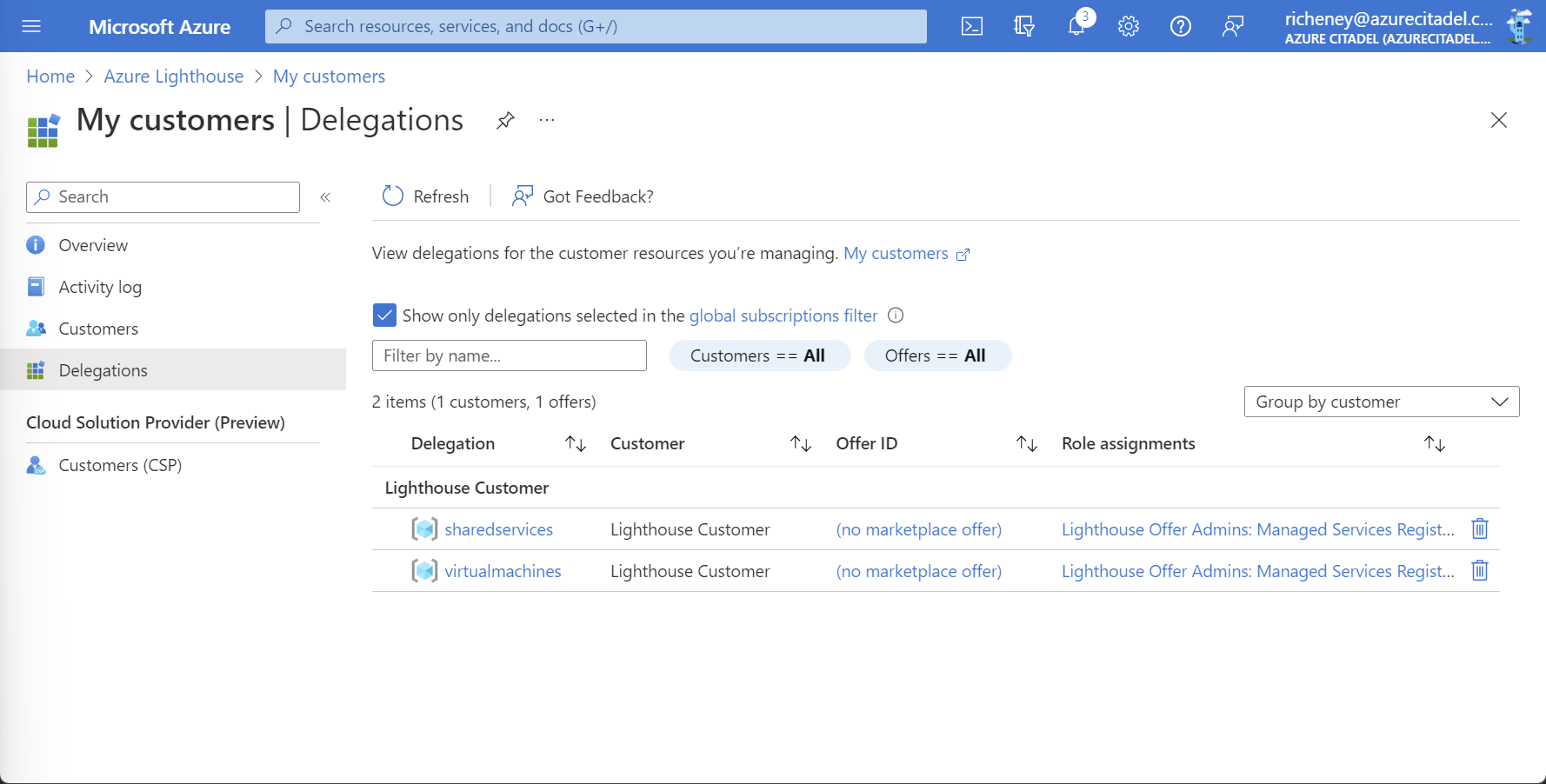
Check the delegations
-
Click on the directory filter at the top of the portal
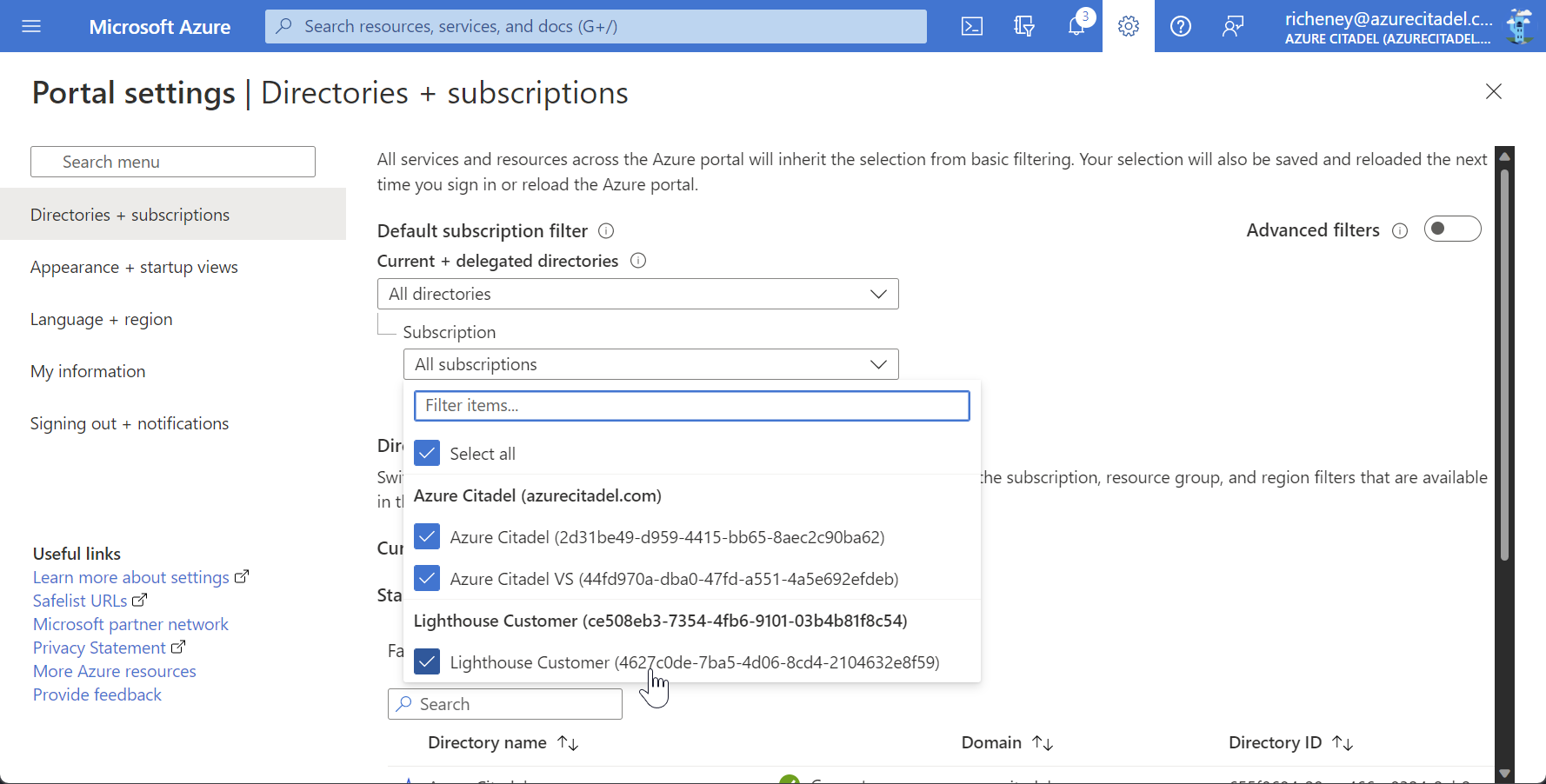
Note that the directory filter now include two levels, for directories (tenants) and subscriptions.
Explore creating and saving advanced filters.
-
Browse resource groups or a resource type to view cross-tenant
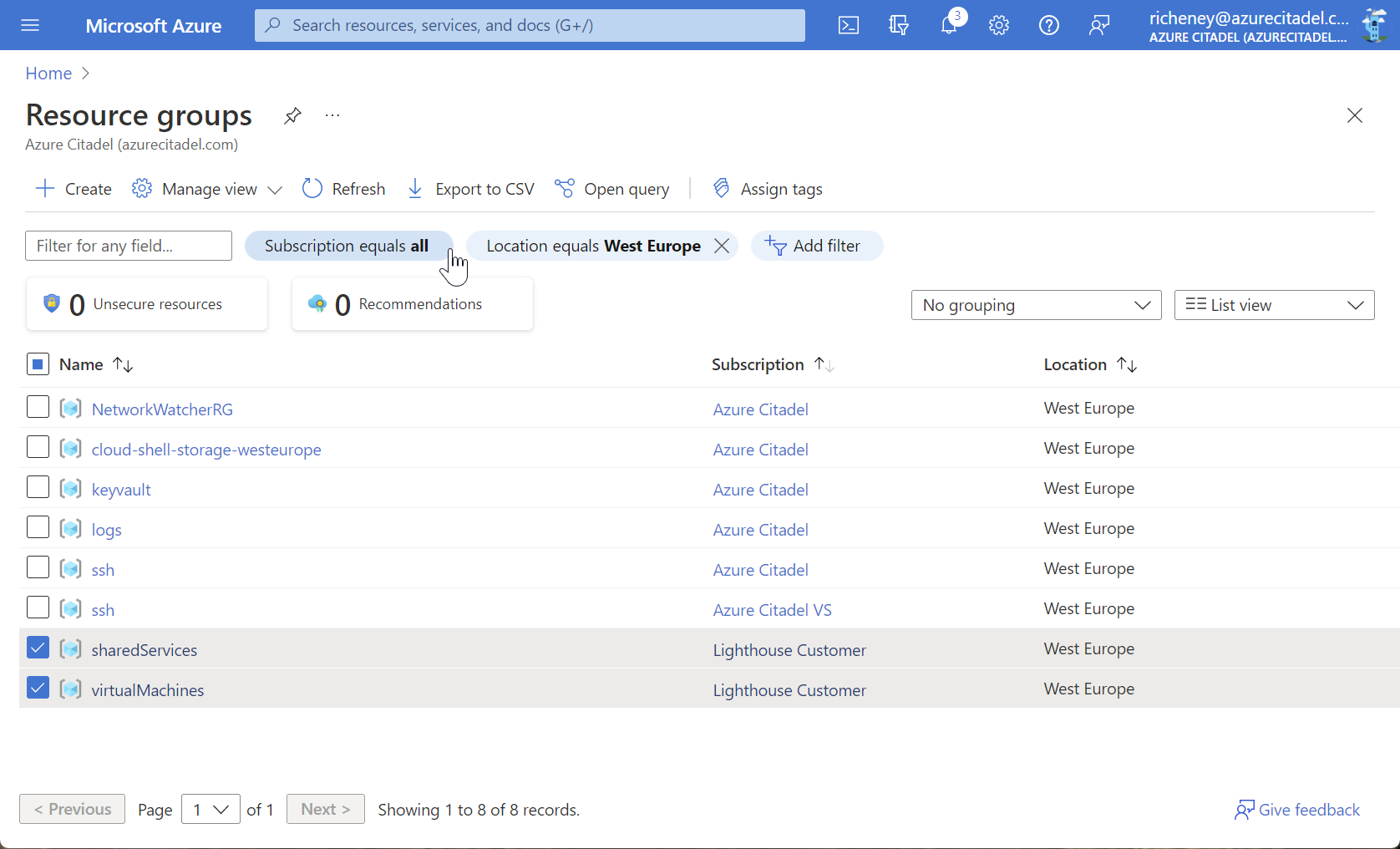
Note that directory or tenant is not yet available as a column. It is recommended to modify the cosmetic subscription names to include a customer identifer.
-
Browse Virtual machines
In the example below you can see the three VMs in my Lighthouse Customer subscription.
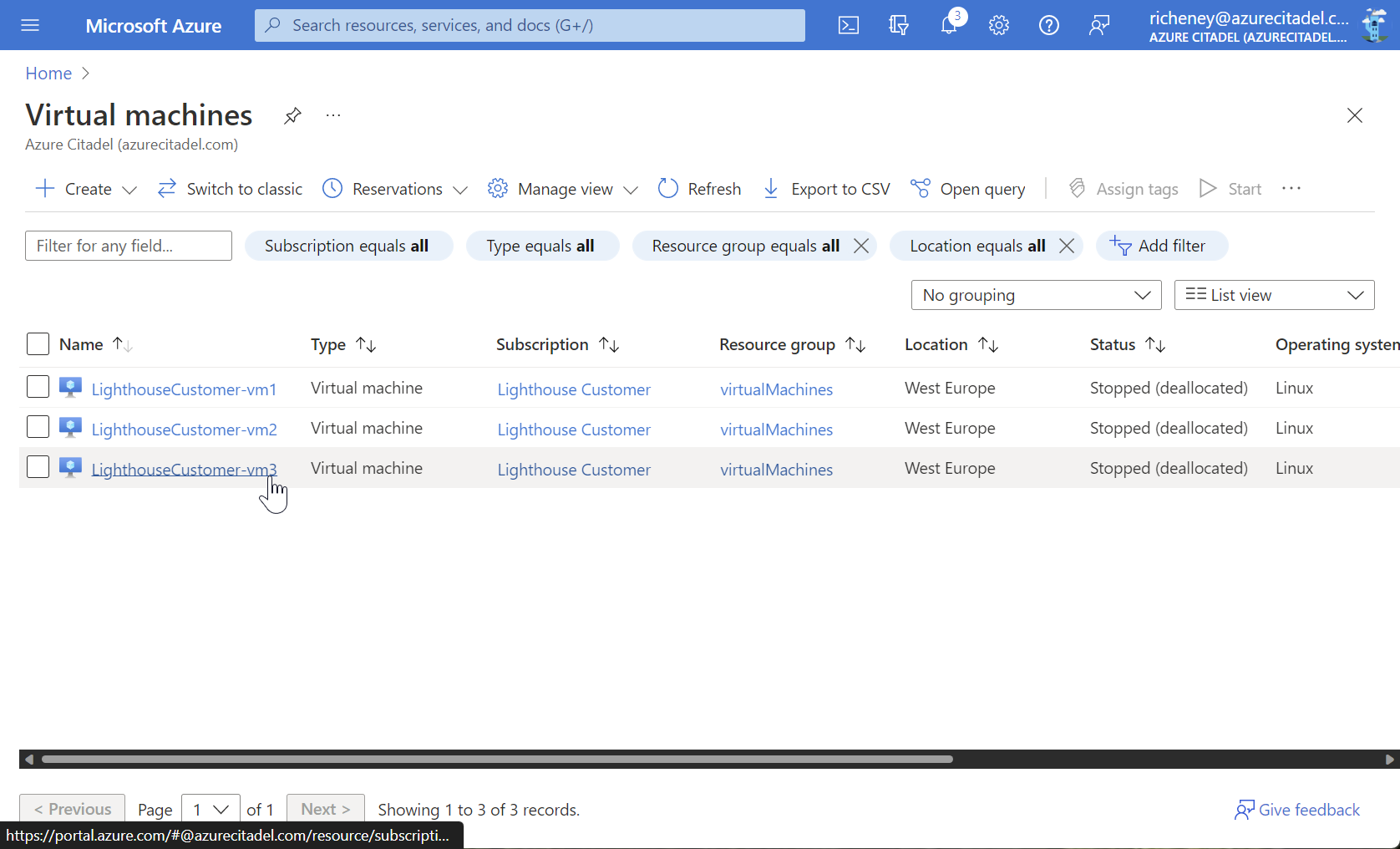
The authorisations in effect are Reader and Support Contributor. (Attempting to start the VM would correctly fail.)
-
Raising a support ticket
Don’t create unnecessary support tickets! This screenshot included for completeness.
In the screenshot below you can see that the reader and support contributor roles are enabling the creating of support tickets.
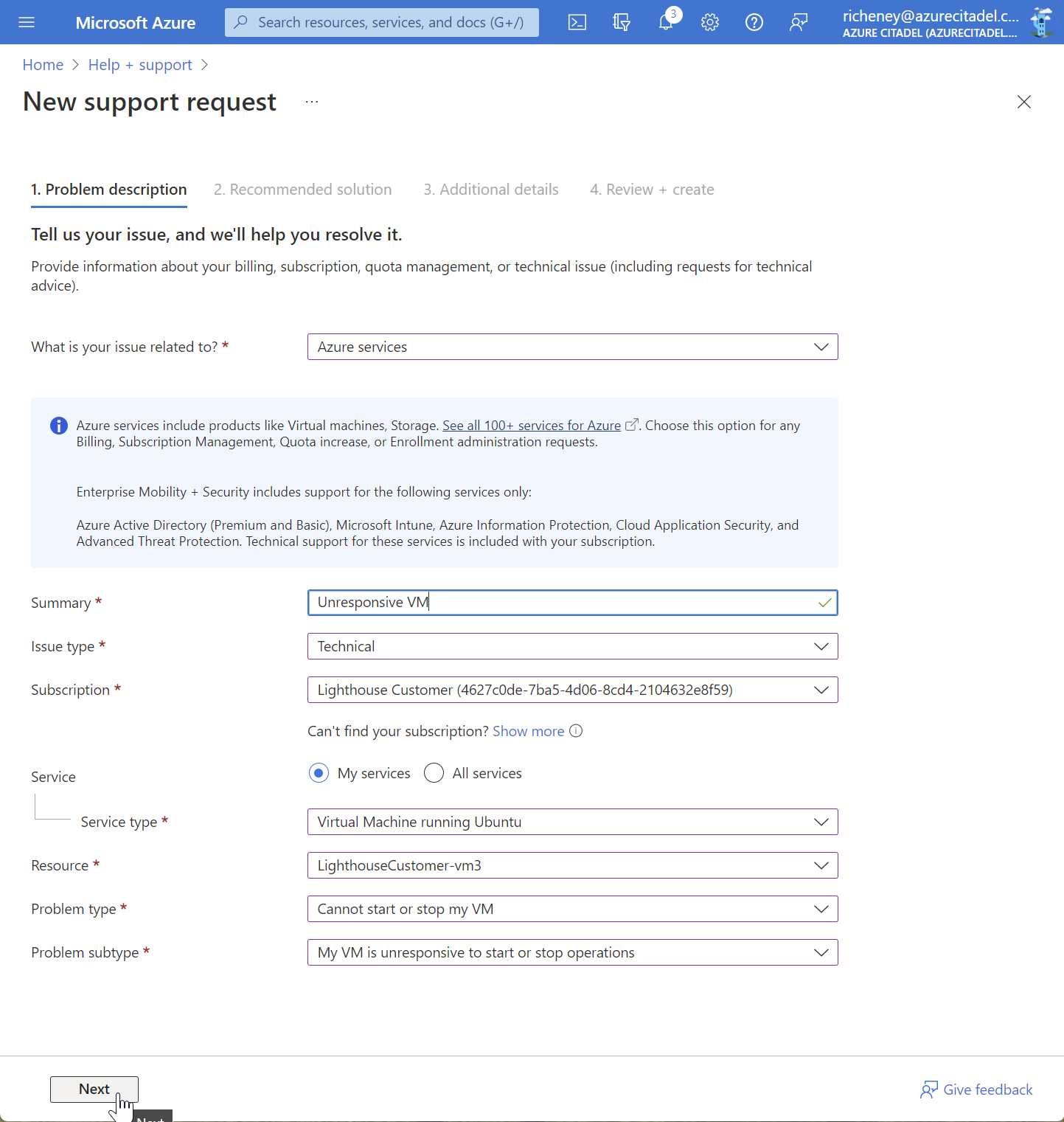
Enabling the multi-tenancy with Azure Lighthouse opens up opportunities with the visibility across resources. Improve support in your managed services, report across your customers with Azure Resource Graph queries and automate at scale via scripting and infrastructure as code.
PAL linking
The Azure Lighthouse definition includes the PEC eligible Support Contributor role, but the customer’s ACR won’t be attached without PAL linking as the definition was created from a template.
Ideally, each user in the security groups specified in the definition’s authorisation should use Partner Admin Link to link their ID to the Microsoft Partner Network ID (MPN ID).
-
Click on Settings in the portal
-
Click on Microsoft partner network in the useful links at the bottom left
-
Enter your MPN ID
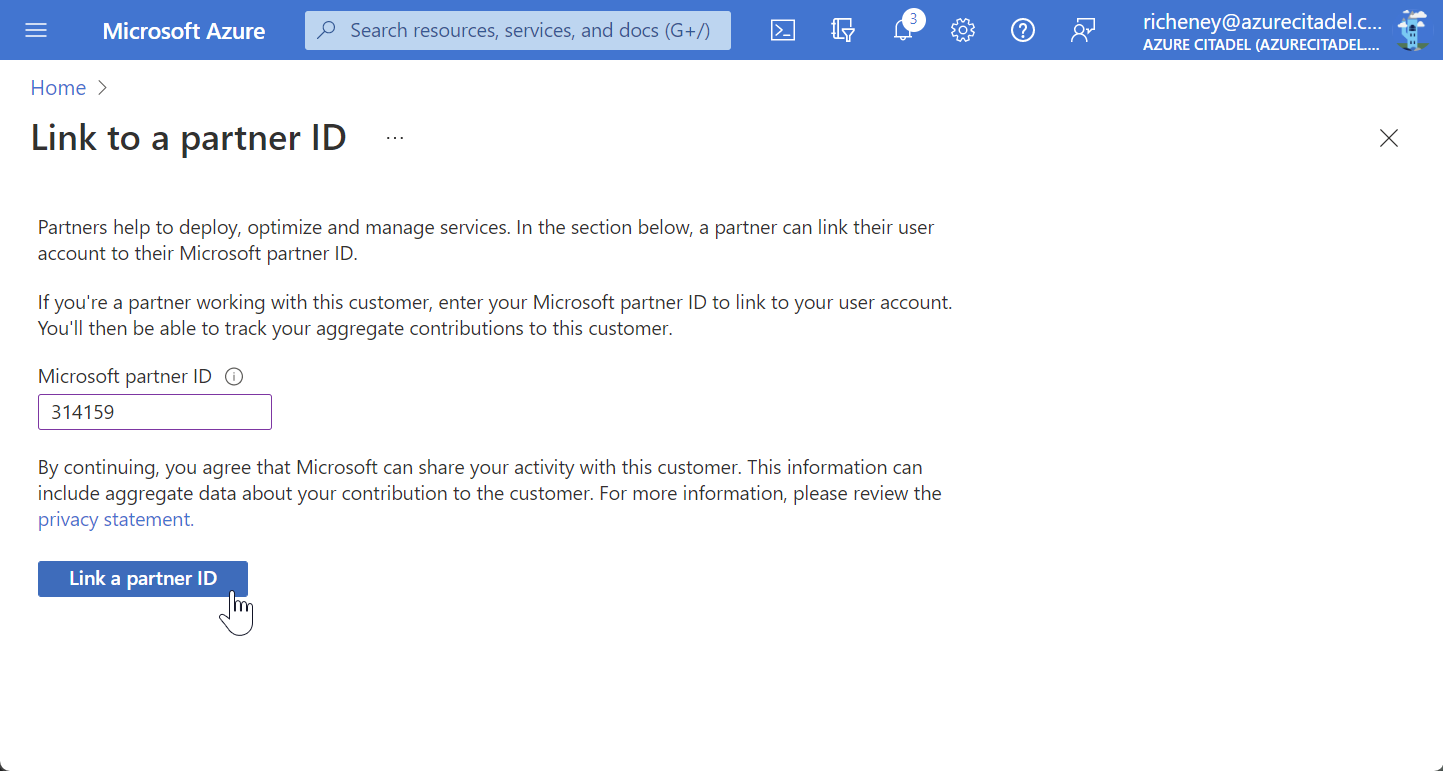
Note that the MPN ID must be a location based ID, not a v-org ID.
-
Click Link a partner ID
Done! It’s that easy.
Linking only needs to be done once for each ID. Note that there is no way to report on which users in the MSP tenant have linked their ID.
References
- Creating Azure Lighthouse definitions
- Example minimal definition
- Azure RBAC built-in roles
- Roles eligible for partner earned credit
- Partner Admin Link
- Publish Managed Service offers to the Azure Marketplace
Next
On the next page we’ll look at using service principals in Azure Lighthouse definitions, show how to use PowerShell or the Azure CLI to authenticate and PAL link.