NVA CSR1000v
Deploy a Cisco network virtual appliance from the Azure Marketplace.
Lab Overview
Let’s look at how to deploy an NVA on Azure. We will deploy a Cisco CSR 1000v router from Azure Marketplace. Note that there are a wide range of network virtual appliances available from several vendors.
Deploy network virtual appliance CSR1000v in Azure
-
Deploy a CSR1000v virtual router in Azure.
- From the portal home page, click on + Create a resource.
- Type “csr” in the search box.
- This should give you a drop down menu on options on how to deploy the CSR. Select option ‘CSR1000v Solution Deployment’ and click Create.
-
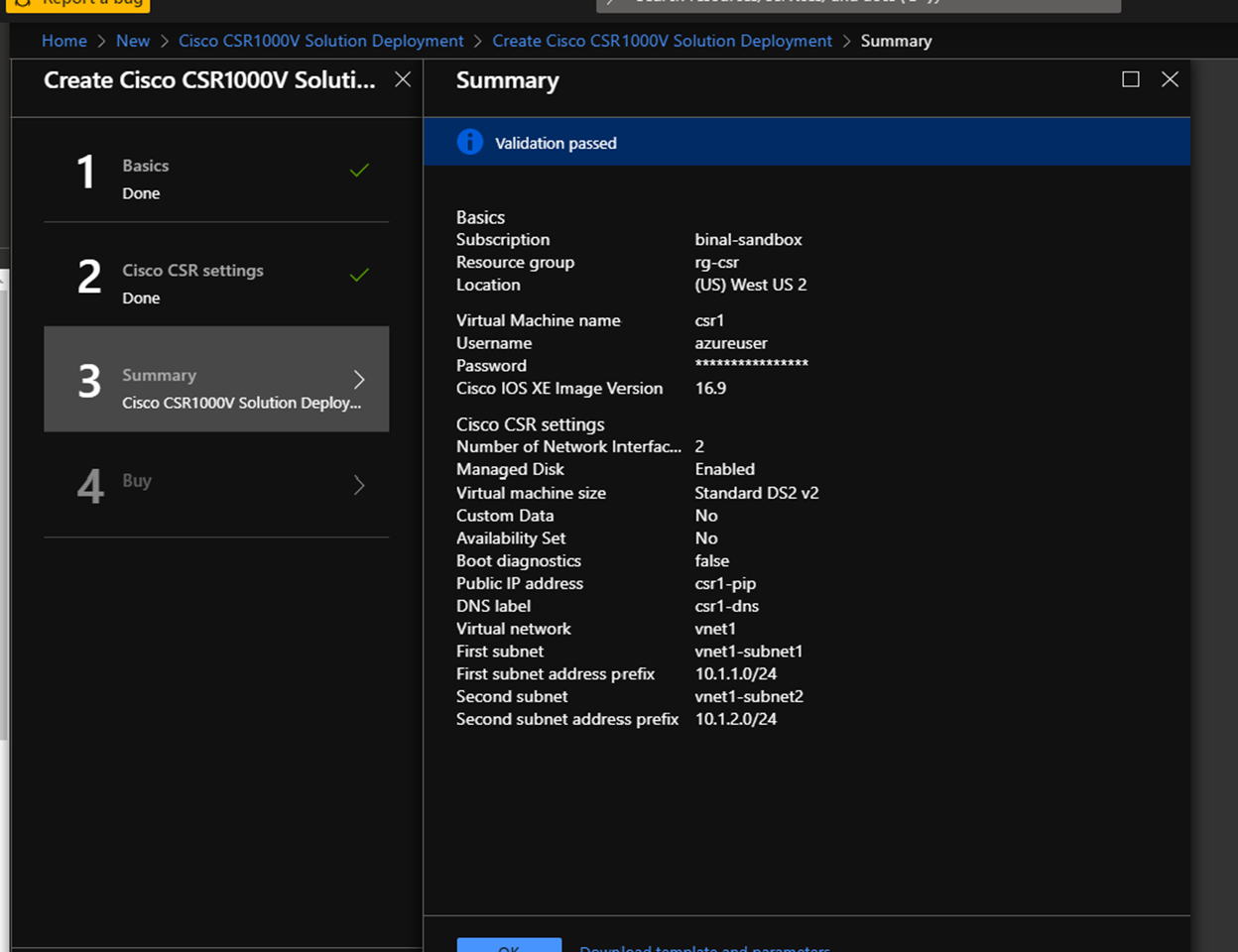
This will bring up a configuration screen for CSR. Follow the steps to complete the configuration and create the CSR. Remember to add 2 network interfaces to CSR. Follow prompts to create a new virtual network. We will use this vnet as simulated on-premises environment.
Setting Value Basics VM name csr1 Username Azureuser Password <password of your choice> Resource Group Click Create new to create a new resource group rg-csr Location West US 2 Cisco CSR settings Number of network interfaces in CSR 2 Availability set For this lab, select No Virtual-network vnet1 First subnet Name: vnet1-subnet1 Address prefix: 10.1.1.0/24 Second subnet Name: vnet1-subnet2 Address prefix: 10.1.2.0/24 -
Verify configuration and click OK to go to the page to buy the CSR. Add your name, email address, phone number and click Buy. Remember NVA charges will apply.
-
Go to the Virtual machines page. You should see the VM ‘csr1’ listed.
-
Once the status of the VM changes to ‘Running’, click on the name. This takes you to the VM overview page.
Connect
-
Once the virtual machine is created, go to the VM and get the public IP.
-
From a terminal, connect to the VM as follows:
ssh azureuser@<public-ip-of-csr-vm>This brings you to the CSR prompt where you can view and configure the CSR.
Verify
Verify that the network security group was applied to the CSR. When you created a CSR NVA virtual machine, a network security group was applied to the CSR interfaces.
- Go to Network Security Groups and find NSG csr1-SSH-SecurityGroup
- Under Settings, go to Network interfaces
- See the network security group applied on the two csr network interfaces
- Verify the Inbound Security rules under Settings
- Review the rules allowed
Help us improve
Azure Citadel is a community site built on GitHub, please contribute and send a pull request
Make a change